Disclosure: Covert Web-to-App Tracking via
Localhost on Android
We disclose a novel tracking method by Meta and Yandex potentially affecting
billions of Android users. We found that native Android apps—including Facebook,
Instagram, and
several Yandex apps including Maps and Browser—silently listen on fixed local
ports for tracking purposes.
These native Android apps receive browsers’ metadata, cookies and commands from
the Meta Pixel and Yandex Metrica scripts embedded on thousands of web sites. These JavaScripts load
on users’ mobile browsers and silently connect with native apps running on the same device through
localhost sockets. As native apps access programatically
device identifiers like the Android
Advertising ID (AAID) or handle user identities as in the case
of Meta apps, this method effectively allows these organizations to link mobile
browsing sessions and web cookies to user identities, hence de-anonymizing users’
visiting sites embedding their scripts.
This web-to-app ID sharing method bypasses typical privacy protections such as clearing
cookies, Incognito Mode and Android’s permission controls. Worse, it opens the door for potentially
malicious apps eavesdropping on users’ web activity.
📢 UPDATE: As of June 3rd 7:45 CEST, Meta/Facebook Pixel script is no longer
sending
any packets or requests to localhost. The code responsible for sending the _fbp cookie has been
almost
completely removed.
📁 Additional Resources
– Video showing Yandex sending localhost requests. The left window shows a
remote debugging inspector window of the browser on the Android phone.
The right window shows the screen of the Android phone, with our proof-of-concept app at the top and
the browser at the bottom:
– Video showing Meta Pixel sending localhost STUN requests. The left window
shows Wireshark, a program that monitors web traffic.
The right window shows the browser visiting a website. Note that the requests only start sending
once the page is loaded when emulating a Android phone (Pixel 7)
and the breakpoint added to the Facebook script is passed:
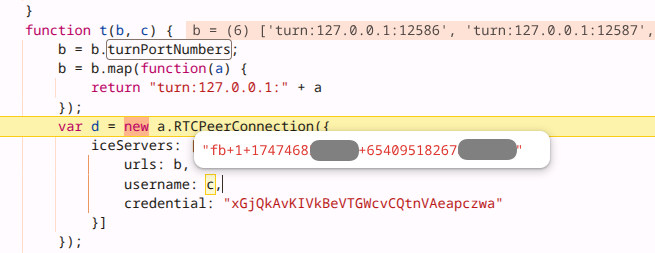
– Image showing Meta Pixel parameters for which ports and protocols to
contact localhost.
![]()
– Image showing Meta Pixel performing SDP Munging to insert the _fbp cookie
value.
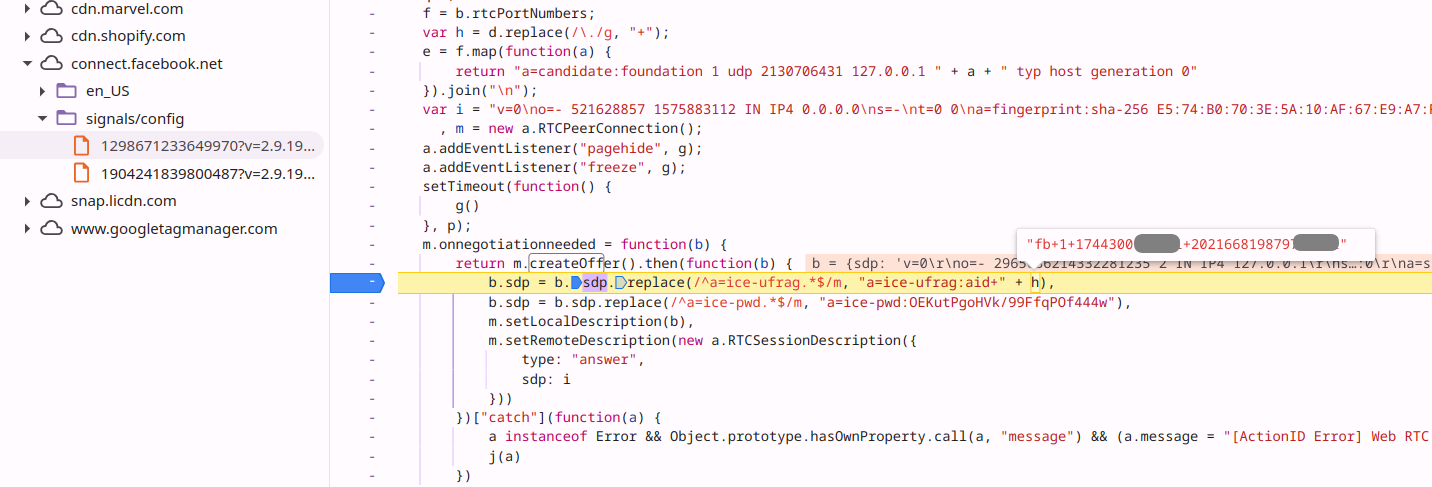
– Image showing Meta Pixel using STUN to _pass fbp cookie value to mobile
apps.